Manage RBAC
This topic describes how to assign an RBAC role for users to get them access to the cluster resources. RBAC is a method to manage users' access to resources based on their roles in a company.
The KubeConfig file contains the token that provides a given user access to the cluster resources.
View the KubeConfig File
-
Go to RBAC on the left sidebar.
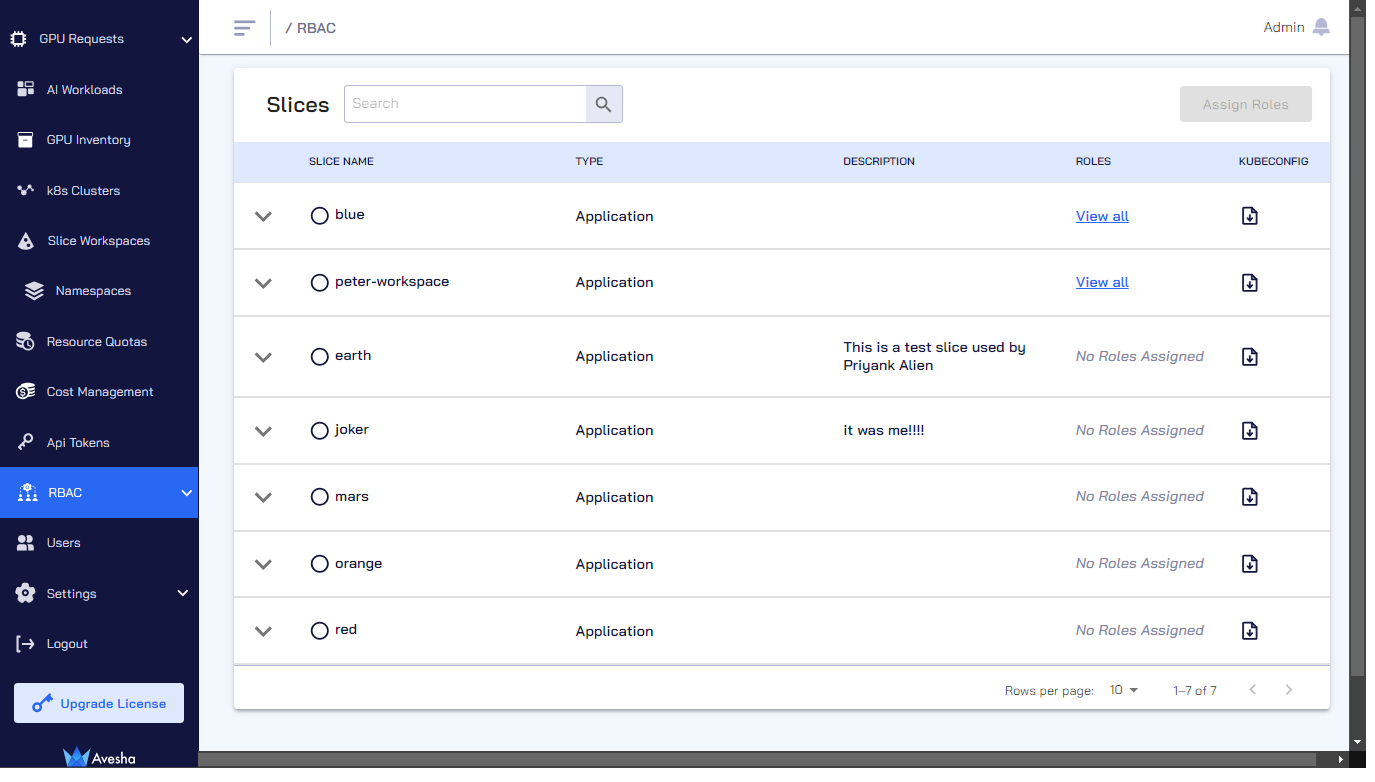 note
noteYou can only download the KubeConfig file for a slice which contains roles assigned under Roles.
-
The KubeConfig file is downloadable only if it has View all under Roles. Otherwise, you must assign roles as discussed in the following section.
-
The user after he logs in to the user portal can download the KubeConfig file from the RBAC page.
Assign Roles
You can assign roles to users or groups to grant them with the micro-level access to a slice.
Admin can edit/modify the default role templates, add new roles, and use them.
To assign a role:
-
Go to RBAC on the left sidebar.
-
(Optional) Check the cluster details for each slice by expanding its menu.
-
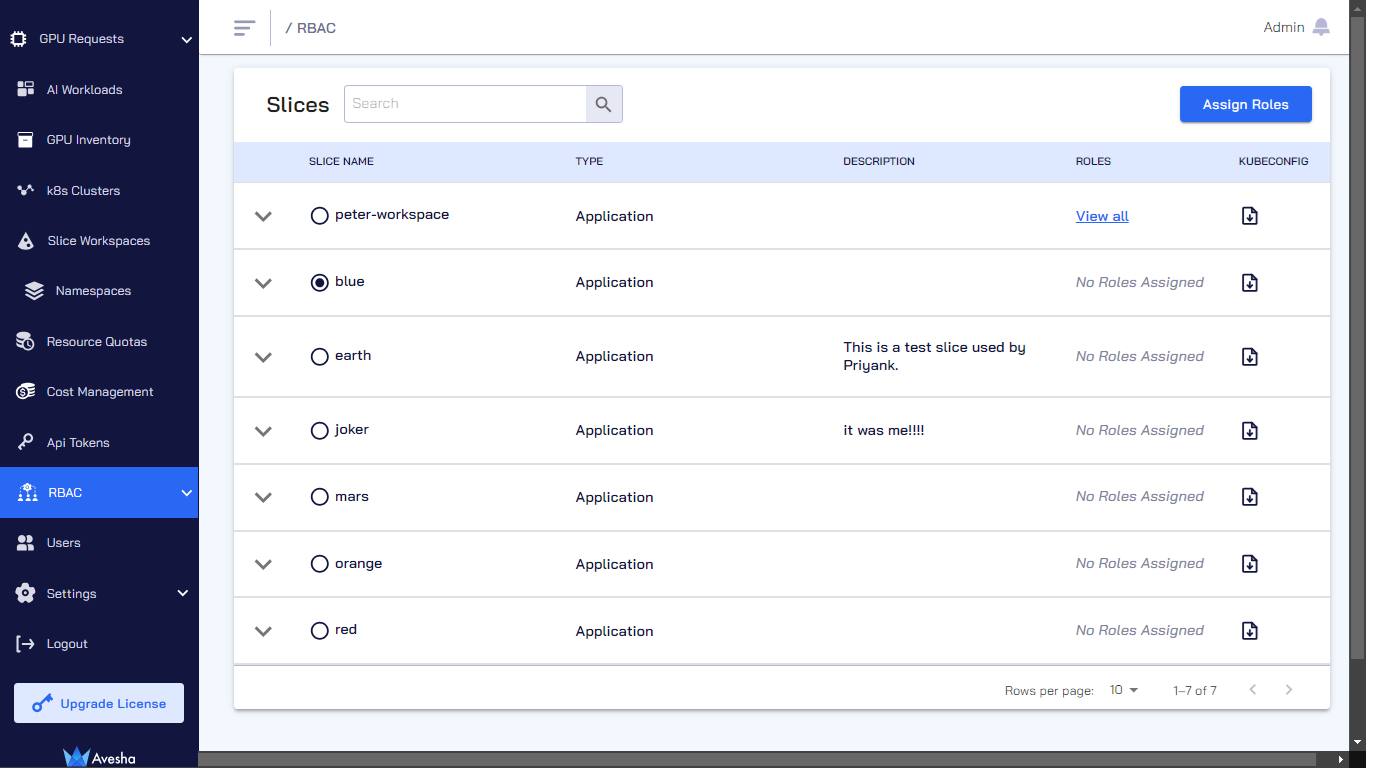
Select a slice for which you want to assign roles.
-
Click Assign Roles. Assigning roles is further divided into four steps as described below.
Step 1 - Assign Roles to the Slice
The first step is to assign roles to users and groups for accessing the slice.
To assign a role to users/groups to accessing the slice:
-
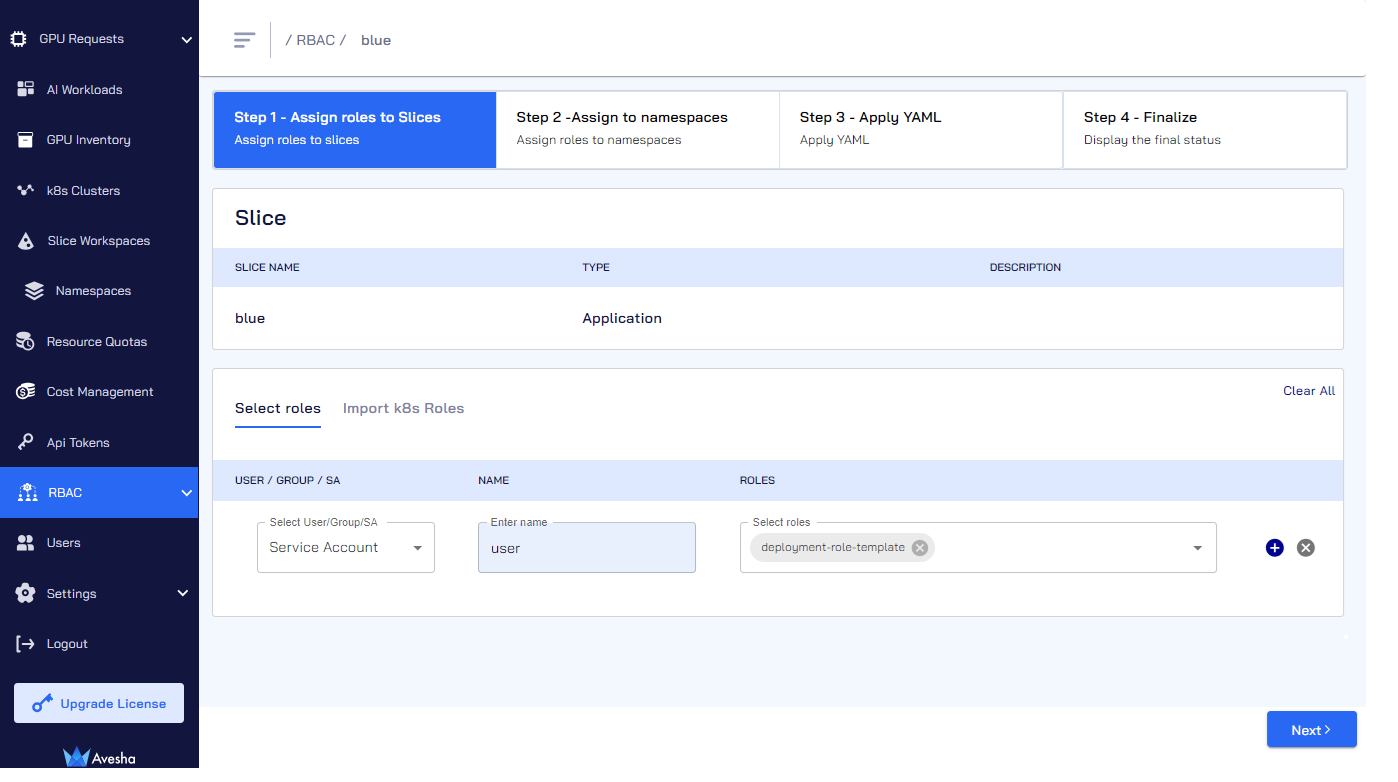
On the Step 1 - Assign roles to Slices tab, you can select roles.
-
Under SELECT ROLES, for User/Group, select Service Account from the drop-down list.
-
For Name, enter the name of the user or group for which you want to assign the role.
-
For Roles, select roles from the drop-down list to assign them to the user or the group.
-
Add another user or group to assign roles (if required) by clicking the
+(plus) icon. -
After assigning roles to the slice, click Next to assign roles to namespaces.
Step 2 - Assign Roles to Namespaces
The second step is to assign roles to namespaces onboarded on to a slice. To assign roles to namespaces:
-
On the Step 2 - Assign to Namespaces tab, you can see that the role in question is not assigned to namespaces.
-
Under Roles, select the role that you want to assign and click Assign Namespaces.
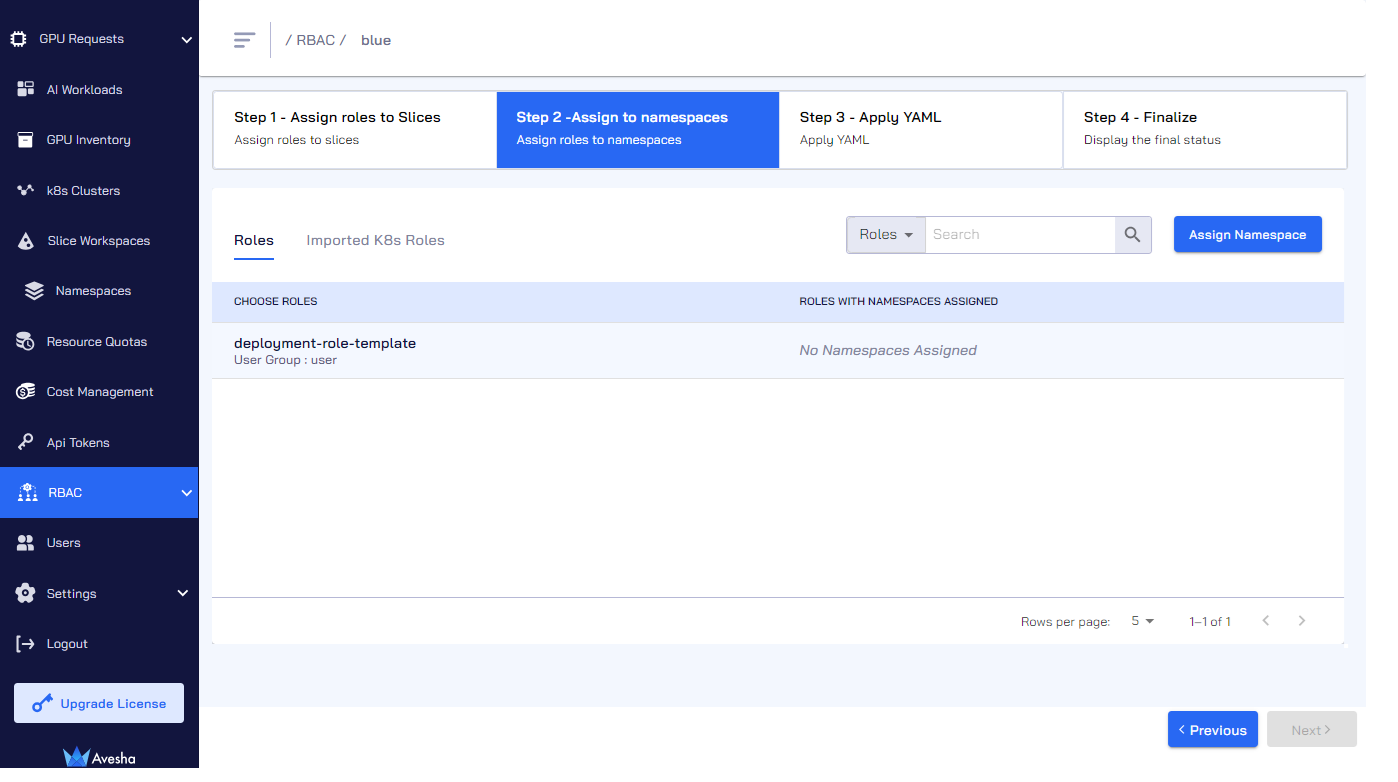
There is a search box in which you can search by Roles, Users, or User Groups. All these three options are in the search box's drop-down list.
-
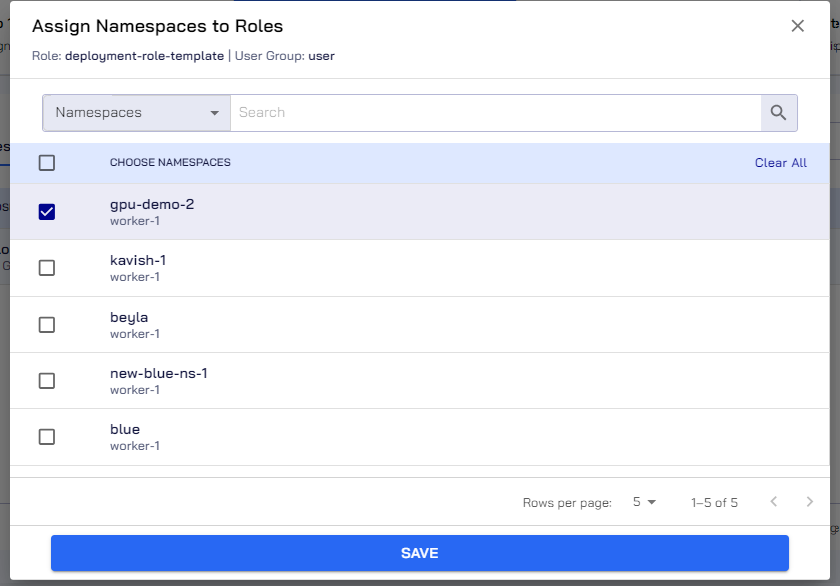
On the Assign Namespaces to Roles dialog, select the namespace that you want to assign this role or select the CHOOSE NAMESPACES checkbox (that is above all the namespaces) if you want to assign the role to all the namespaces.
-
Click Save to assign the role to namespaces.
-
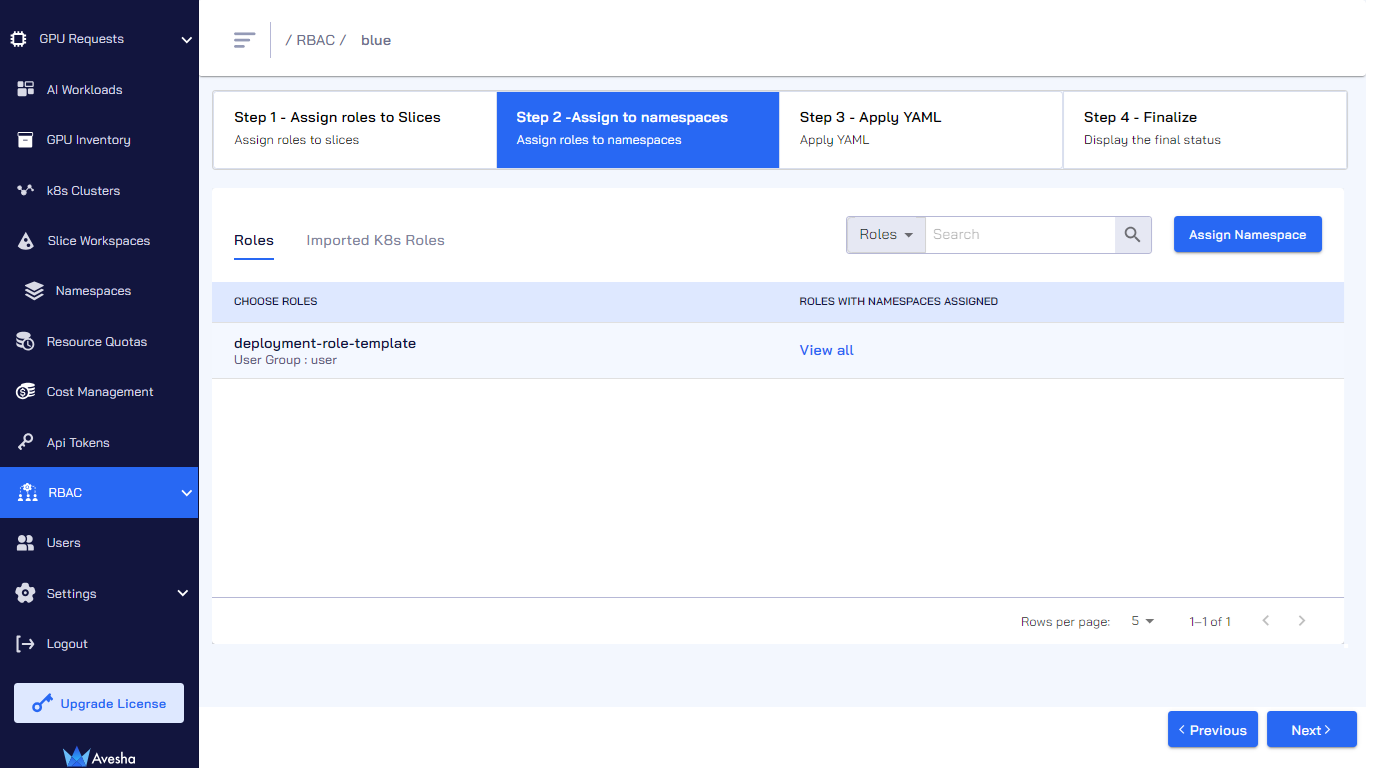
On the Step 2 - Assign to Namespaces tab, verify the list of namespaces assigned with a role by clicking View all for that specific role.
-
Click Next to apply the YAML file.
Step 3 - Apply YAML
The third step is to apply the YAML file that is autogenerated. To apply the YAML file:
-
On the Step 3 - Apply YAML tab, under the Code Preview, verify the configuration.
-
Click Apply YAML to apply the configuration.
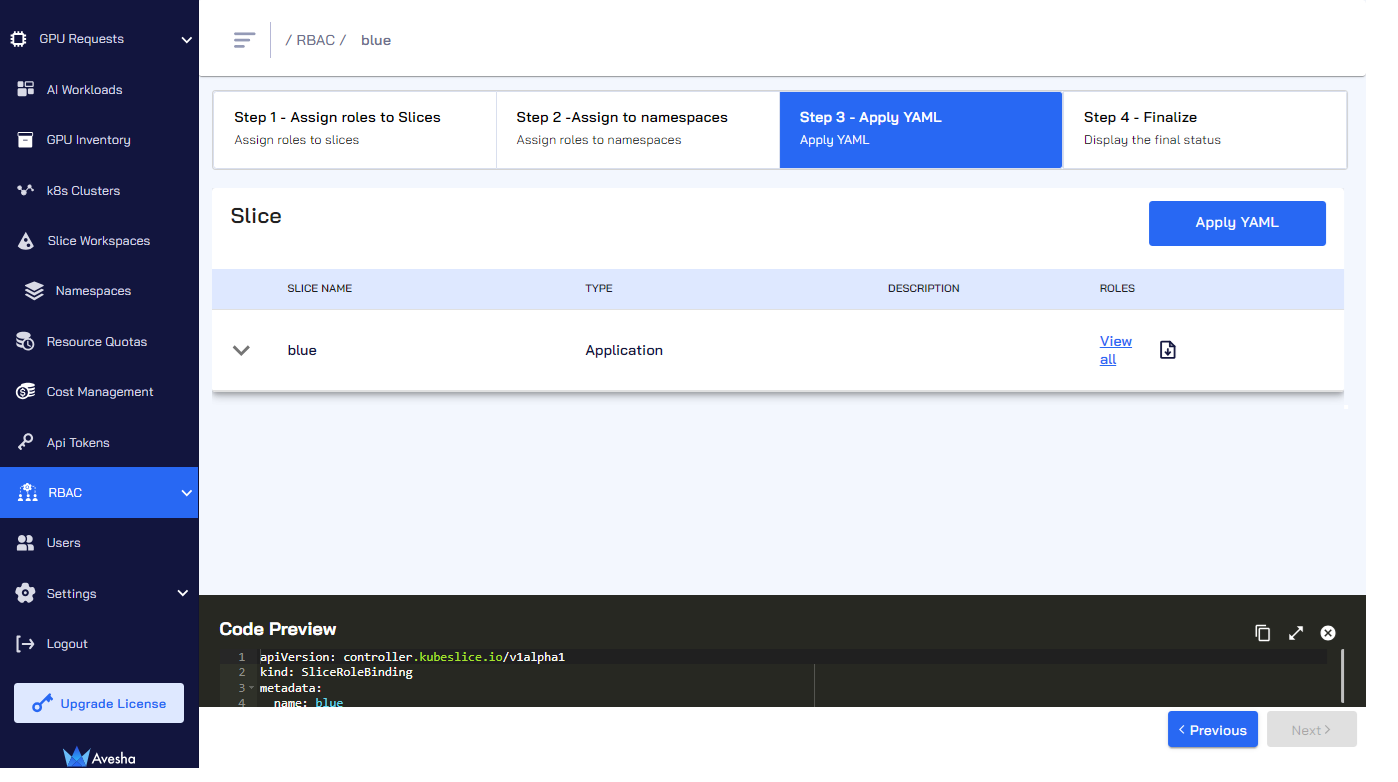
- Click Next to finalize all the configuration.
Step 4 - Finalize the Role Assignment
The fourth step is the final step to verify the role assignment.
To verify the role assignment:
-
On the Step 4 - Finalize tab, verify the role assigned to namespaces.
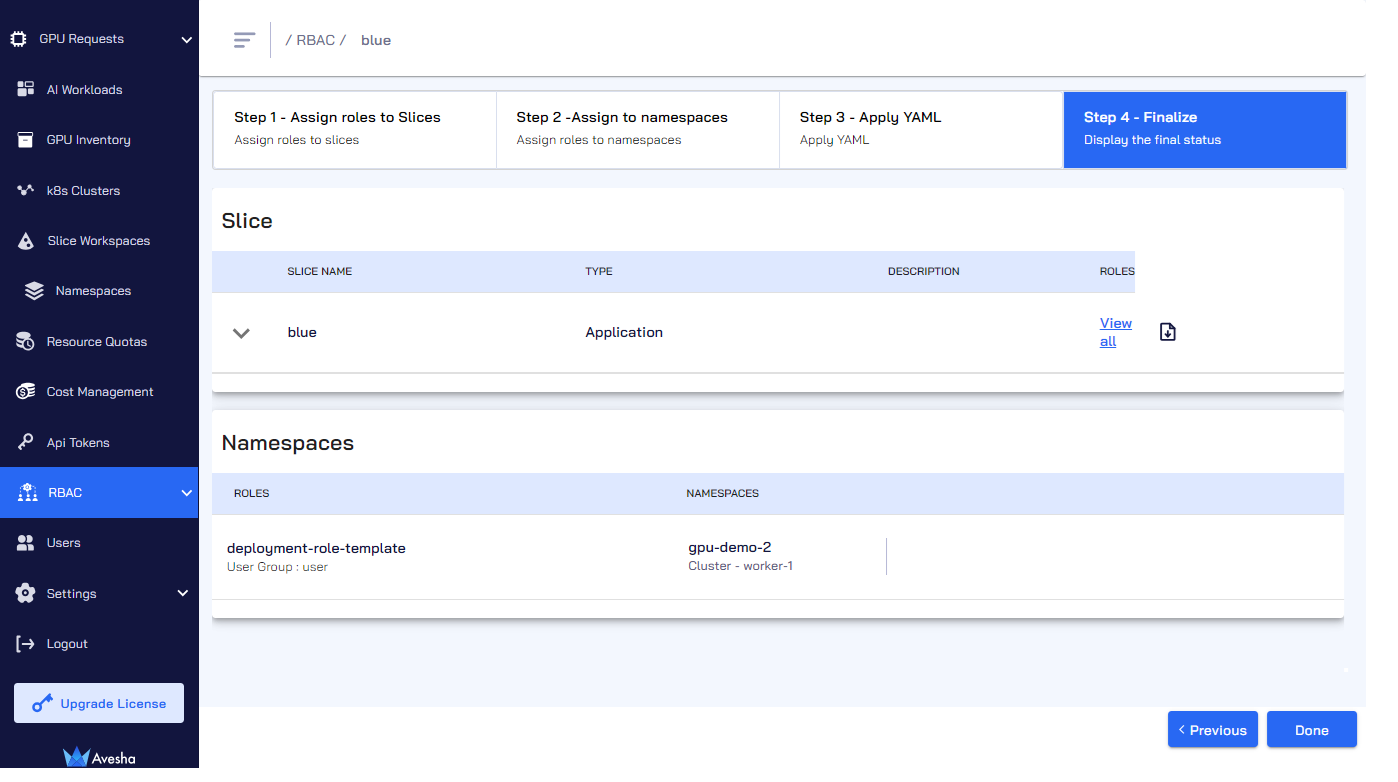
-
Click Done. On the RBAC page, the roles assigned to a slice.
Download the KubeConfig File
A KubeConfig file can be downloaded when a Service Account is attached to some roles. If you are using User or Group attachments to the roles, then use the IDP provided configuration to access the worker clusters.
To download the user token for a slice, on the RBAC page, from the Slices list, click the download button under KUBECONFIG.
Share the KubeConfig File with the User
The downloaded Kubeconfig file contains appropriate privileges as defined in the RBAC. Share this file with the user to grant access to the clusters.